Back in 2014, in our ACM WiSec paper, entitled WifiLeaks: Underestimated Privacy Implications of the
More particularly, we found that 41% apps (out of a total of 2700 most popular apps tested) were accessing ACCESS_WIFI_STATE permission. It was very a surprising result because this permission gives access to Wi-Fi related information (MAC address, BSSID of connected access point, Wi-Fi scan info, etc.) and we could not imagine why so many apps would require to access this information. The only apps we could imagine requiring access to such information were Wi-Fi configuration apps or local area network based game apps for example.
By looking more closely at these Wi-Fi related information, we found that it may reveal a lot of personally identifiable information like a device unique identifier (MAC address), Wi-Fi scan info (to derive approximate geographic location), etc.
We then looked further into the apps and statically analysed all those apps that required ACCESS_WIFI_STATE permission. To our surprise, we found that apps in almost all the categories (even apps in wallpapers and comics category) are calling Java methods (that are protected by this permission) to access aforementioned Wi-Fi related information. Below is the figure from our paper which depicts the categories of apps requesting this information.
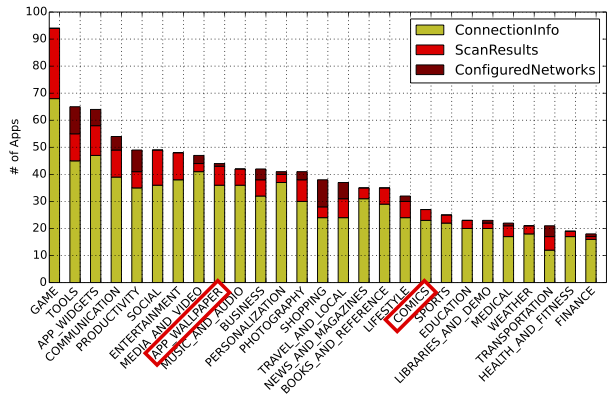
Category wise distribution of apps accessing ACCESS_WIFI_STATE Android permission
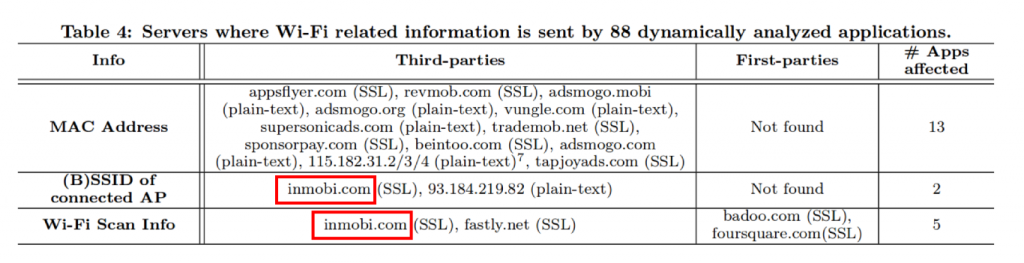
We dynamically analysed 88 apps (those apps which looked interesting to us based on the results from static analysis) to check if these apps really access and send this information over the Internet. We found that is was the case for the third party library of InMobi that was accessing Wi-Fi related data and sending it back to their servers (See figure below).
The result of the Wi-Fi Scan Info collected by InMobi can be used to derive the location of the device. Indeed, this information is the list of nearby Wi-Fi access points (identified by their BSSID) which can be used to obtain the geolocation of the device using trilateration techniques. This method is actually used by most mobile Operating System to obtain a geolocation without relying on the GPS, but the resulting geolocation information is always protected by the geolocation permission. However, we found that many of those apps who use InMobi are in fact not requesting the geolocation permission but surreptitiously computing it by abusing ACCESS_WIFI_STATE permission on Android.
Two years after our research was published, the Federal Trade Commission (FTC) reached a $950,000 settlement with InMobi for tracking millions of consumers’ locations, including children, without their knowledge. The FTC allege that InMobi abused the WiFi State information on the Android system to track the location of people without their consent, which is exactly what we showed in our research. Its policy prevents the FTC of releasing the sources of its investigations, therefore there is no way to affirm that our research triggered this investigation or was used during this investigation. We can only be sure that we identified a privacy issue that was serious enough to justify an investigation of the FTC and a penalty of $950,000. In fact, the penalty is actually 4M$ but the FTC is only asking 950K$ because the company would be bankrupt otherwise. In addition to this, the company is under surveillance for their privacy behaviour for the next 20 years.
Back in 2014, we also conducted a survey and found that users do not really understand the privacy implications of this ACCESS_WIFI_STATE permission. The permission looks innocuous but it is really not.
This is because a variety of private information could be derived using the data accessible from this permission (again, check our ACM WiSec paper). Android OS marks its protection level as ‘normal’ (even though location could be derived from the information accessible through this permission) whereas location permissions are marked as ‘dangerous’. As the permission description does not explicitly describe all the possible privacy implications and users do not really understand these privacy implications, we contacted Android security team to report our findings in 2014. They acknowledged reception of our mail and told us that our mail is forwarded to the Internal team. However, the permission is still marked as ‘normal’ and its description is not yet changed.
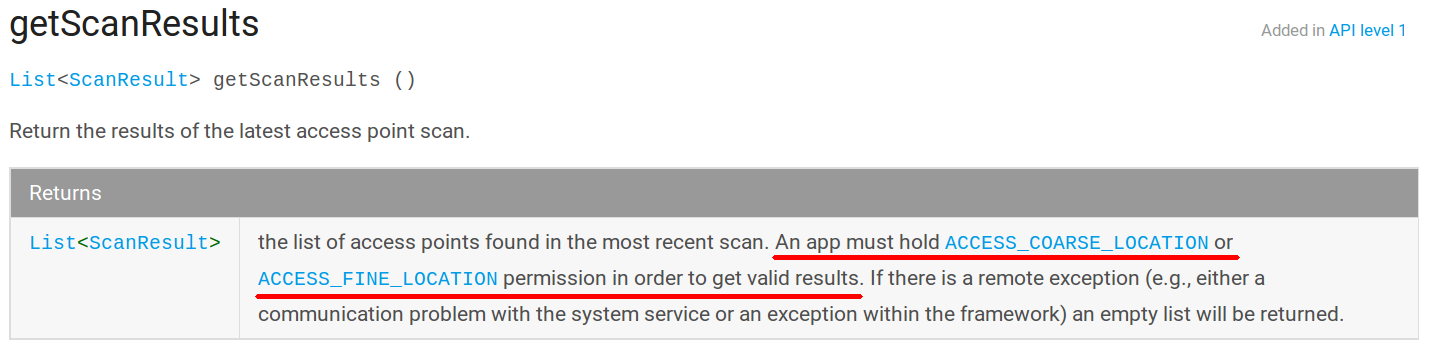
Update: Although the permission description has not been modified, the Android system has been modified to reduce the privacy issues. More specifically, the getScanResults method, which give access to the list of nearby Wi-Fi access points and thus the location, is now protected by location permissions. However the getConnectionInfo method, which exposes the device’s location through the identifiers of the currently connected network, is still only protected by Wi-Fi permissions and not by location permissions.
We hope this ruling will lead advertisement and analytics companies to think twice before abusively collecting sensitive information without being clear about the data collection.
This research is a joint work between Inria Privatics team and Eurecom. It has been partially supported by the Inria CAPPRIS initiative.